Reward your researchers fairly – try our bug bounty calculator today!
Agile security testing, powered by the crowd
Secure your assets with our community of ethical hackers
Intigriti specializes in crowdsourced cybersecurity services that help organizations protect themselves from cybercrime and data breaches.
Our industry-leading bug bounty platform enables companies to tap into our global community of 125,000+ ethical hackers, who use their unique expertise to find and report vulnerabilities in a secure process to protect your business.
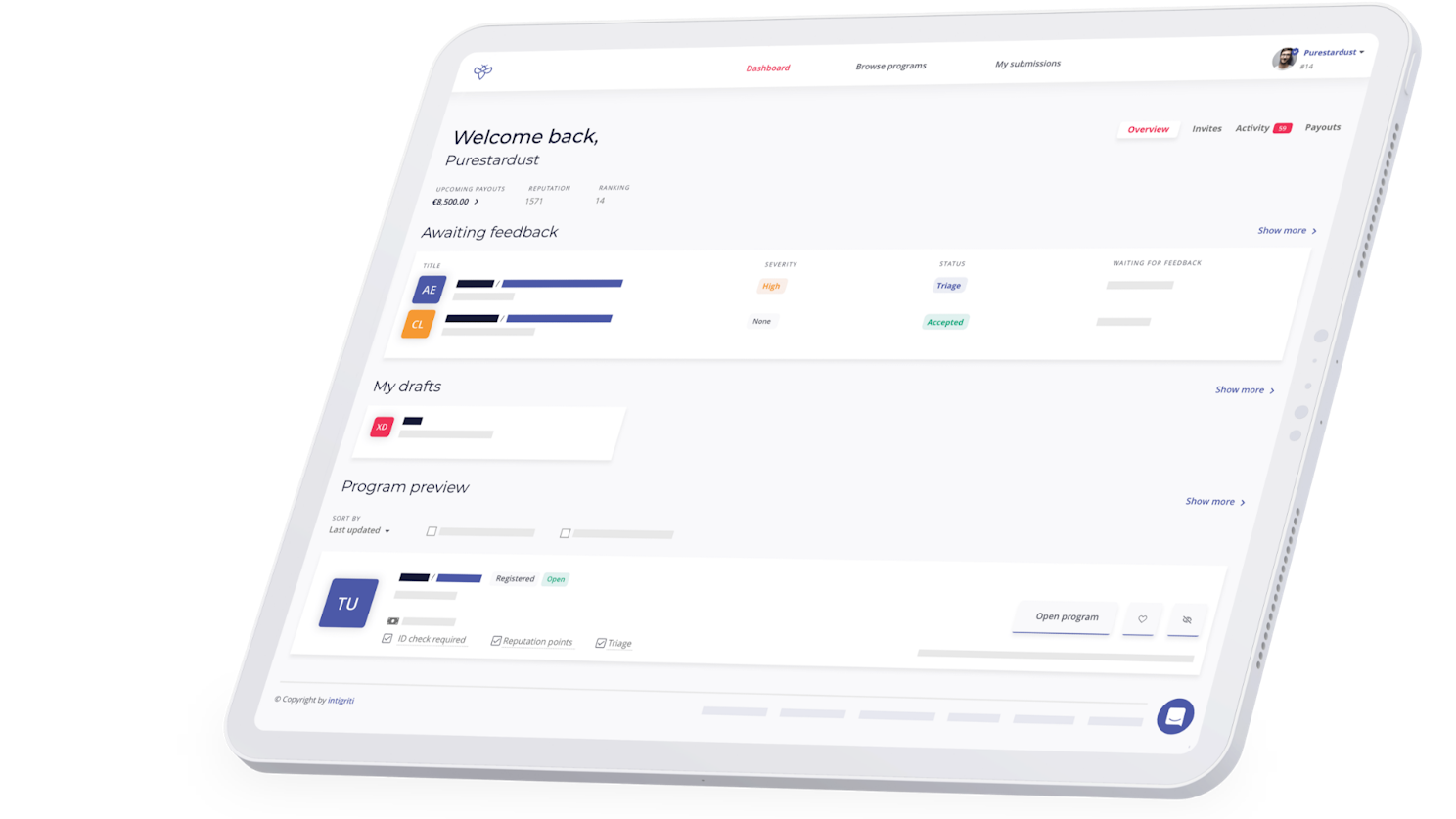
Take a platform tour
Ready to experience Intigriti's platform in action?
Take a live demo and explore the dynamic capabilities firsthand. Empower your security and development workflows with our multi-solution SaaS platform, that can merge into your existing processes.
Expert hacking community
Our community of ethical hackers discover vulnerabilities and improve your security.
Our close-knit community management ensures you are connected with the right hackers that suit your requirements.
Triage support
All reports are validated by our expert triage team and managed via our platform.
With our focus on quality over quantity, we promise an extremely competitive triage lifecycle for clients.
Security certifications
We support your compliance requirements and are ISO 27001 and SOC 2 certified.
Our Trust Center is a live dashboard that provides insight into our security and compliance posture.
The platform integrates with
More than a bug bounty platform
Intigriti is a crowdsourced security company that enables our customers to access the highly-tuned skills of our global community of ethical hackers.
Our services can be divided into these main categories:
Our clients include
How Intigriti is helping organizations
More than 200 organizations including Intel, Yahoo!, and Red Bull trust our platform to improve their security and reduce the risk of cyber-attacks and data breaches.
About us
Founded in 2016, Intigriti has a global team of employees based in Belgium, the UK, the Netherlands, and South Africa.
Our mission is to lead the path to global crowdsourced security and make ethical hacking the number one choice for companies and security researchers.
How it works
Whether you are launching a VDP, bug bounty, or PTaaS, setting up a crowdsourced security program with Intigriti is simple:
Choose your program
Our customer success team is on hand to help you determine which program is best for you.
Select your crowd
You call the shots by setting the terms of engagement and whether your bounty program is public or private.
Boost your cybersecurity
Once your program is launched, you will start to receive security reports from our ethical hacking community.
Optimize your program
We help you optimize and modify your VDP, bug bounty program, and Penetration Testing for long-term success.
Frequently asked questions
A vulnerability disclosure program (VDP) enables businesses to mitigate security risks by providing support for the coordinated disclosure of vulnerabilities before they’re exploited by cybercriminals. By hosting your VDP with Intigriti, you remove the headache of managing and triaging any incoming reports from ethical hackers.
These two services are suited to different needs. A traditional pentest is a great way to test the security of your assets, although they tend to be time-boxed exercises that can also be extremely expensive. A bug bounty, meanwhile, gives continuous security protection over time, where the bounties are open to a wide cross-section of ethical hackers.
For those in search of some middle ground between a penetration test and a bug bounty, Intigriti’s Pentest as a Service (PTaaS) is perfect for fast, targeted checks on assets. These time-bound pentests use expert members of our hacking community. This SaaS-based approach to vulnerability assessment and penetration testing marks a new chapter in enterprise cybersecurity.
A Live Hacking Event allows ethical hackers to gather in person and collaborate to complete an intensive inspection of an asset. These high-profile events are ideal for testing mature security assets and are an excellent way to showcase your company’s commitment to cybersecurity.